Sandwich Attacks in Crypto: How to Prevent Them?

What Are Sandwich Attacks in Crypto?
The attacker finds a pending transaction in the network and intentionally “sandwiches” it by putting orders just before and after the targeted transaction; this technique is also called front-running and is a kind of maximal extractable value (MEV) attack. You should know that there are various MEVs, including front-running, back-running, manipulation of transaction orders, and more.
Because all transactions are available on the mempool before approval, these attacks typically target decentralized finance (DeFi) services and decentralized exchanges (DEXs). The immutability of the blockchain makes it easy for malicious actors to search for big pending transactions to hack, even though this is an essential aspect of the system.
How Do Sandwich Attacks Work?
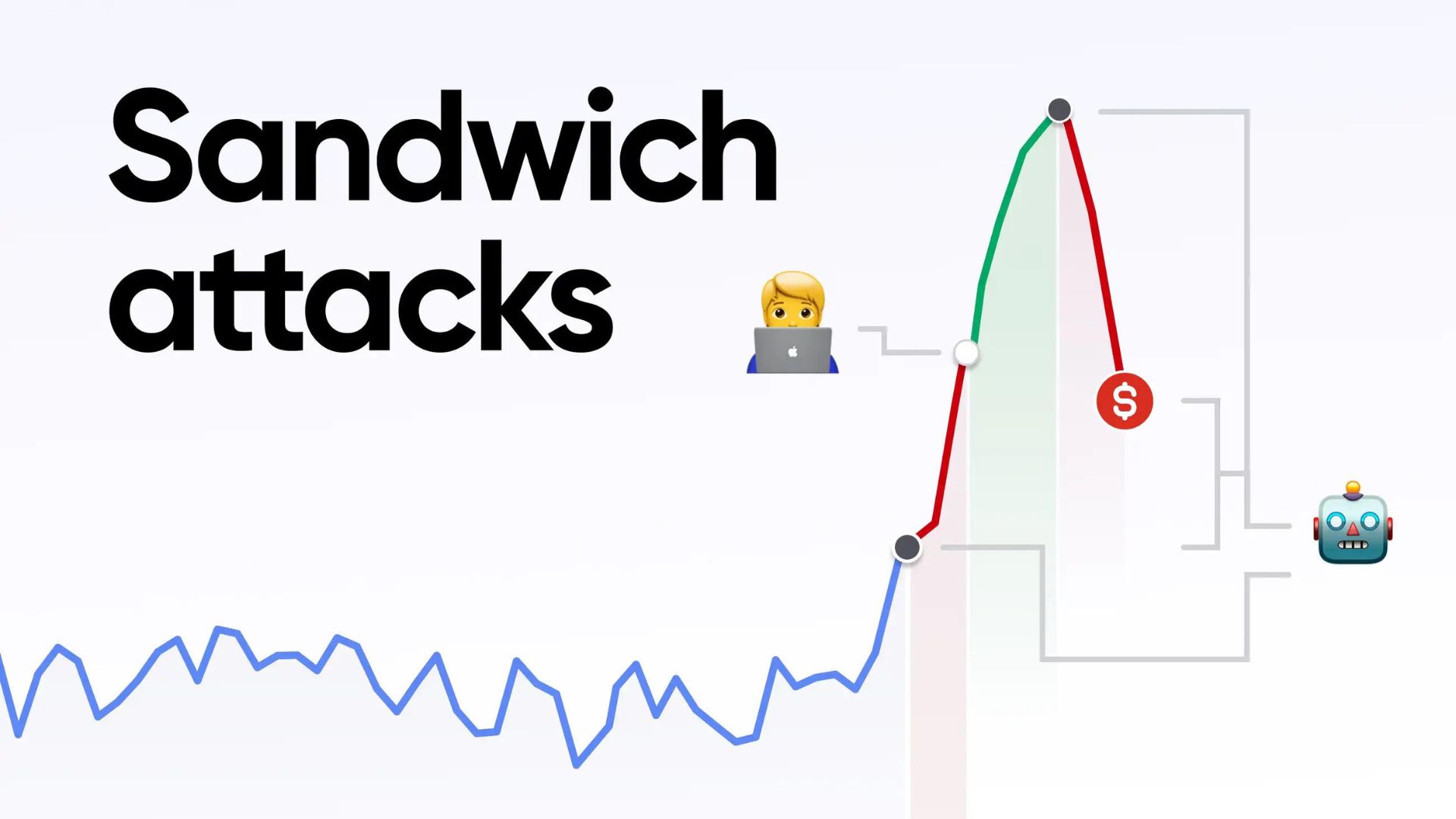
The employment of a bot allows an attacker to bypass blockchain security measures and conduct larger transactions ahead of schedule. So, the perpetrator will use the bot to buy a huge amount of gas right before the victim’s transaction is about to go through, paying exorbitant fees to get their transaction approved first. When an attacker buys a token ahead of time, it boosts the victim’s token’s price. The attacker then sells the token at a profit, taking advantage of the victim’s transaction. As a result of the transaction inflating the attacker’s sell order, the attacker can profit from the artificially inflated price difference. At the same time, the victim typically incurs a substantial financial loss.
Anyone following the cryptocurrency market for any time has probably heard of Jared from Subway.eth, the notorious bot that made about $34 million in three months using just sandwich attacks. According to Dune, the top gas user on the Ethereum network is jaredfromsubway.eth, who has spent over $90 million on gas thus far. This makes him more expensive than prominent crypto firms such as Binance and Crypto.com.
Your holdings are typically the targets of such assaults, so it’s wise to be aware of the precautions you might take to safeguard them. You should also know that sandwich attacks are not yet officially forbidden; therefore, protecting your valuables is up to you.
Set a Low Slippage
When a transaction’s real price differs from its expected stated price, this discrepancy is called slippage. The rapid pace of market activity is to blame for this shift; while you attempt to complete your trade, the value of an asset could rise or fall within seconds. If your slippage tolerance is 10%, for instance, it indicates that you’re open to accepting the transaction at a price that’s 10% above or below the price you were quoted when you started the deal. But your purchase will not go through if the price changes by more than 10% or less.
Your transaction will only be approved if the token price stays within a specific range, as indicated by the low slippage setting. Sandwich Attacks in Crypto: As a result, your deal will be cancelled and not processed if an attacker makes a large purchase before you and the token price increases more than your slippage tolerance. Even if the attacker buys just enough tokens to go within your slippage range, a low slippage overall will prevent them from making much money off the attack, protecting your tokens.
Typically, the suggested slippage tolerance of 0.5-1% should be more than enough to handle the typical price fluctuations. Remember that a failed transaction and gas wastage could occur if the slippage is too small. Several factors, including individual assets, token taxes, market volatility, and more, should be considered when adjusting your slippage tolerance.
Use Larger Liquidity Pools
Also, when you do a transaction, aim to employ larger liquidity pools. A liquidity pool is a group of funds bound together by a smart contract, which DEXs need to process transactions. A more stable trading environment is created when the liquidity pool is larger, as they tend to be less volatile. Because of this, they can also reduce the impact of individual transactions on the overall pricing.
As a result, an attacker would need a lot of money to launch a sandwich attack in a big liquidity pool and generate the price swings that would benefit them. This can be a deterrent since sandwich attackers would need a lot of money to alter the price.
Pay Higher Gas Fees to Prioritize Transactions
To mitigate the risk of sandwich attacks, traders can utilize more gas when doing transactions, particularly when dealing with larger trade amounts. Using less gas could reduce expenses, but the attacker can detect and carry out the attack more quickly. The transaction will complete faster with more gas, and attackers will require far more gas to front-run it. This acts as a disincentive against attackers targeting the transaction because it is costly for them to do so, requiring high gas. Users should carefully assess their options to protect their assets, as high gas can frequently be expensive.
Utilize Telegram Bots

Automated Bitcoin trades are now within your reach using Telegram bots that may link straight to your wallet. While a vast array of bots are available today, most have common characteristics such as the ability to copy trades, support for multiple wallets, liquidity, method sniping, anti-rug and honeypot protection, and stop loss and take profit orders. There are features available in some Telegram bots that could help you avoid sandwich assaults.
Most Telegram bots include a private transaction feature that lets users conceal trade data until they are conducted, protecting them from sandwich attacks. An attacker can scan the blockchain for pending transactions to attack before a transaction is confirmed because the transaction is already available on the mempool. Sandwich Attacks in Crypto: To prevent MEV bots from front-running transactions, it is recommended that they keep transaction data hidden under the private function until the last possible moment.
Unibot, Mizar, and Banana Gun Bot are just a few Telegram bots that now include a private transaction feature. Also, remember that the bots can access your private keys, which could compromise your security. A security breach at Unibot cost the platform $630,000 in October 2023. Users should always take the required measures to protect their assets, even though Unibot reimbursed those harmed by the exploit. These features are convenient, but they are not infallible.
Use a Private RPC Network
Programs can talk to the blockchain via an RPC node, which stands for remote procedure call. Right now, most traders are using open-source, publicly accessible RPC endpoints. Sandwich attacks can happen when attackers scan the mempool and see the pending transactions, as stated above. Traders can conceal their pending transactions by submitting them directly to the Ethereum network over a private RPC network.
Run Your Node
One option to accomplish this is to operate your node. By establishing your node, you can submit transactions directly and hide them from attackers. By decreasing reliance on third-party systems, you’ll also have greater control over your transactions, including when and how they’re processed.
MEVblocker
To further safeguard your trades from MEV, you can utilize MEV Blocker, a free RPC endpoint. As stated on the website, traders’ transactions are sent to a network of searchers that look for back-running possibilities but cannot front-run your trades. This is how MEV Blocker accomplishes its job. Users can add MEV Blocker to their MetaMask or other cryptocurrency wallet.
Flashbots
Flashbots, despite their name, are not automated computer programs. Flashbots, a research and development company, focuses on researching and studying Miner Extractable Value (MEV). The group’s objective involves combating front-running and other unethical trading activities to ensure users have a fair and equal opportunity. Sandwich Attacks in Crypto: The company provides various products to users, validators, infrastructure providers, and bot operators. Aside from Flashbots Builders, Flashbots MEV-Share Node, and Flashbots Protect, they provide a range of other products.
‘Flashbots Protect’ can be easily integrated with Ethereum wallets like MetaMask for traders. Not only does this function safeguard traders from MEV bots front-running them, but it also provides additional features like preventing users from having their transactions reversed. By establishing a connection to a private RPC network, the Flashbots Protect feature enables users to bypass the public mempool and send their transactions straight to miners, protecting them against MEV assaults.
Conclusion
While blockchain technology was created to promote transparency and trust among users, sandwich attacks inadvertently take advantage of this quality. The particular set of difficulties investors have in the cryptocurrency market stems from the fact that it is still less regulated than traditional financial markets. New types of assaults will certainly emerge as cryptography develops further. Traders and investors should be alert to the dangers of unfair trading activities to protect their investments more effectively.