That’s Why No One Can Crash a Blockchain

What Makes a Blockchain Withstand Hacks?
Decentralized and Open-Source Protocols
The distributed aspect of a blockchain network is achieved by utilizing numerous computers or nodes. By doing so, we remove a potential weak spot. To rephrase, “cutting the head off the snake” is not an option because the snake does not have a head. No One Can Crash a Blockchain: The blockchain’s design defines how nodes in a blockchain work together to confirm a transaction before adding it to the protocol. To commit to a transaction in Bitcoin or any PoW system (including Bitcoin Cash), at least 51% of the nodes must agree.
Hashing Algorithm
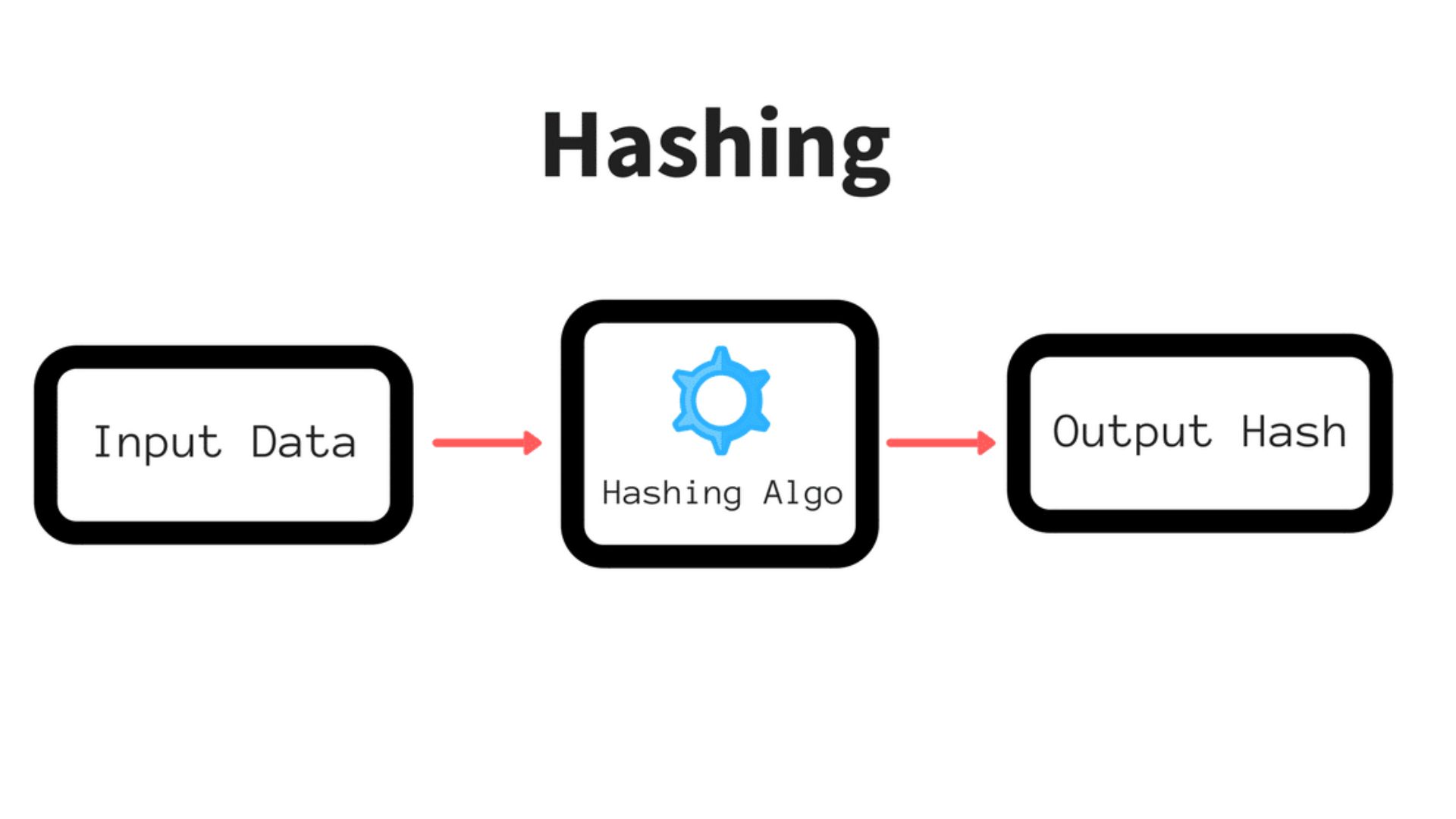
A blockchain is an interconnected record of many transactions, where each transaction is called a block. Notably, cryptographic features provide each block its own identity. The network’s hashing algorithm decides the specifics. One example is the 256-bit hash mechanism the Bitcoin blockchain employs, which compresses and hashes transaction data twice.
A transaction gets rigid when it becomes difficult to undo the hashed value. A unique collection of information from the block before it is included in each subsequent block in a chain. Thus, the system will reject any block that is not in sync with the others due to its differing hash output, even if an attacker were to reverse-engineer the hash.
51% Attacks Are Improbable
What About Quantum Computing?
The fact that an attacker would have to re-hash earlier blocks to align their historical stamp with the current block makes hacking a blockchain much more difficult, especially if it is in the middle of the chain. Until the next generation of quantum computers is developed, this will not be achievable for Bitcoin. Who says there won’t be a way to protect against quantum assaults using blockchain technology? And that’s assuming it happens.
PoS-Based Hacks
No One Can Crash a Blockchain: The stakes determine the power of a PoS-based network. To clarify, this refers to users who have allowed other users to conduct transactions or discover new blocks using their native blockchain assets or who have locked them. Assaults occur when hackers obtain control of the majority of stakes on such sites. This becomes feasible once the hacker controls over 51% of the total circulating currencies. This is extremely difficult, if not impossible, for trustworthy networks like the ever-developing Ethereum 2.0 platform. Think about the difficulty of raising $68 billion to purchase 51% of Ethereum’s present market cap!
Economics of a 51%
The purchase of coins will cause their availability to surge in value to extremely high levels, making it impossible to execute a stealth 51% attack without causing scarcity. On the flip side, other participants in the blockchain will sell their coins when they discover you control most of them, which will cause the market to fall due to excess supply. So you’ll wind up spending more money than you make!
How Do Blockchains (Rarely) Get Hacked Then?
The Future of Blockchain Hacks
No one has managed to breach a blockchain on their own. Instead, the core development team or a gang of bad actors usually work together to crack a blockchain’s security. However, the likelihood of hacking a decentralized network is progressively decreasing as blockchain platforms strengthen themselves through increased stakes or nodes. Plus, modern blockchains employ tried-and-true methods that would necessitate supercomputer-level quantum computing power to crack.
In conclusion, you are now equipped to (politely) rebuke someone and send them on their way the next time you hear the phrase “blockchain was hacked!”